Cybercrime poses a constant threat to businesses and their customers, with criminals committing fraud by stealing identities or using phishing to illegally gain access to a company’s computer network.
In recent years, cybercriminal attacks have caused major consumer information breaches at retailers, on social media platforms, and with credit information providers. Seventy-four percent of companies have been the targets of attempted or actual payments (check, wire, or ACH) fraud.
The pace of attack increased in 2020, with two-thirds of companies reporting an increase in fraud attempts since the COVID-19 crisis began.2 And anti-fraud professionals are almost unanimous in predicting an increase in fraud.2 Cybercrime attacks — from ransomware to payments fraud — show no sign of going away.
“Many dealers don’t think hackers are looking at them,” explains Erik Nachbahr, Certified Information System Security Professional (CISSP) and President and Founder of Helion Technologies, an IT/cybersecurity services provider exclusively serving the needs of auto and heavy truck dealers. “Dealerships are increasingly a target of cyber threats with their high volume of large dollar transactions and lack of digital security.” As criminals develop more sophisticated cybercrime techniques and states implement stricter consumer privacy legislation, cybersecurity and data protection should be top priorities for dealers. That means heightened security to ensure data privacy, combat potential attacks, and mitigate losses.
According to the 2021 IBM/Ponemon “Cost of a Breach Report,” it takes an average of 287 days to identify and contain an attack. Data breaches that took longer than 200 days to identify and contain cost an average of $4.87 million, while those that took less than that cost an average of $3.61 million. Lost business accounted for 38% of the overall cost, including increased customer turnover, lost revenue from system downtime, and additional marketing expenses to overcome damage to the business’s reputation.3
Key Dealership Cybercrime Threats
Dealerships generally have a complex technology architecture that makes cyberattack protection challenging. “Many dealership computer systems have hardware added in a one-off manner, are built without a complete system plan, and utilize older, outdated software. In some cases, they underpower their virus protection by using freeware software. Further, weak security protocols that allow user account sharing can undermine a dealer’s business,” Mr. Nachbahr explains.
Increasingly sophisticated ransomware attacks targeting dealerships are on the rise. “These criminals know dealerships have money and are aware of dealer vulnerabilities. That makes dealerships a lucrative target,” continues Mr. Nachbahr. “The attacks aren’t typical automated intrusions; they are enterprise-grade attacks with live hackers combing through a dealer’s systems. Because dealers have many, disparate components and don’t tend to use standard protocols, once their systems are exploited, the breach is difficult to fix.”
Other cyber threats focus on personally identifiable information (PII) which can be stolen and resold to bad actors. Forty-four percent of data breaches included customer PII, making it the number one type of data stolen.3 Dealerships regularly handle vast amounts of PII, particularly financial information, so it’s no wonder they’re an attractive cybercrime target.
In today’s environment, protecting dealership computer systems and their customer data is essential. “As cybercriminals are becoming increasingly adept, more dealers are realizing an attack could be a ‘business-ender.’ Forward-thinking dealers are investing in technologies that protect against these full-scale attacks. Information technology security is now being viewed as a priority, not simply an expense to be controlled,” states Mr. Nachbahr.
The Cost of Cybercrime
The likelihood that a business will experience financial damage after a cybercrime attack is rising quickly. The average cost of downtime from a ransomware attack has doubled over the past year to $274,200.4 The average downtime is now 19 days, a three-fold increase from 2019.2
Direct economic losses are compounded by lost revenues from operational disruptions, brand reputation damage, and decreased customer loyalty. A 2021 IBM/ Ponemon Institute survey found that a data breach costs U.S. businesses an average of $180 for each accessed/stolen record containing customer PII.3 For dealerships with thousands of records, the damage can add up quickly, not to mention the impact on customer relationships. A Ping Identity consumer attitude survey reported that 25% of respondents would stop using a business after a data breach.6 The potential for cybercrime to inflict direct losses, reputational damage, and customer loss highlights the importance of making data security and cyberfraud defense a priority.
A salesperson responded to a phishing email, opening a malicious file with ransomware and providing cybercriminals access to that computer. The salesperson did not suspect an intrusion. Once behind the firewall, the hackers were able to access the dealership’s entire system and servers. The hackers used the compromised computer to probe the network, looking for vulnerabilities to lock up the dealership’s computer operations.
The criminals were able to shut down the dealership’s systems for over a week — asking for payment in bitcoin to relinquish control of the systems. All of the dealership’s servers and emails and one-third of their 300 computers were inoperable. They chose not to pay the ransom, but instead took the next month to rebuild their systems completely. How could this cyberattack have been prevented?
- Through employee education on the hazards of downloading unsubstantiated files or clicking on suspicious links
- With proper web filters and controls to block hazardous links
- By implementing fraud software to quickly find, mitigate, and recover information compromised by fraud and ransomware attacks
Limiting Primary Fraud Threats
When it comes time to address criminal activity targeting payments, banking transactions, customer data, communications, and computer systems, it is important to analyze both non-cyber and cyberfraud. Equally important is identifying the sources of threats — internal and external — and dealing with each accordingly. Simple protection measures along with insurance for business crime, cybercrime, or data breaches can dampen losses. Measures to limit risks include:
- Employee education is the top method for lowering the risk of fraud in general, and cyberfraud in particular. A company culture that values overall fraud prevention sends a powerful signal to employees. Employee education about fraud awareness is one of the best ways to get started. Fraud barriers include:
- Clearly defined fraud prevention roles and responsibilities for you and your employees
- Separation of duties, checks and balances, and multi-factor authorizations for funds transfers
- Secured computers with password protection, changed periodically
- Restricted user account access to individual owners with no shared access
- Web filters and controls that block clicks on potentially fraudulent links
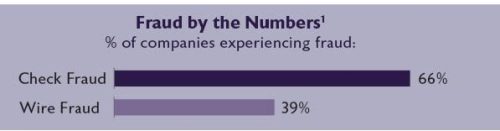
- Check and wire fraud are the top two payment fraud threats for any business. Sixty-six percent of companies reported that check payments were subject to fraud, and 39% were victims of wire fraud attempts.1 Dealership payment volumes — both paper and electronic — make an attractive target for fraud. Implementing a few simple, inexpensive processes can protect your dealership:
-
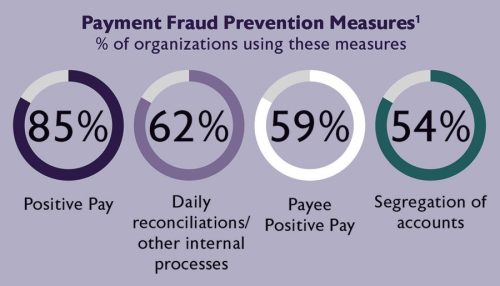
- Use positive pay services. You’ll be able to verify the authenticity of checks by looking over the issue date, check number, amount, and payee name to catch check fraud.
- Protect check stock with dual authorization before use.
- Further enforce authorization through online banking platforms which require additional authentication for wire transfers through assigned user ID and password logins, requestor authentication, and dual approvals.

- Phishing and social engineering attacks scam employees into believing an email is from a reputable company or dealership employee. The recipient then reveals sensitive information, passwords, and credit card or account numbers. Phishing emails can appear to be from the dealership owner, ordering large sums to be wired to external accounts, which then vanish moments after the transfer. Phishing emails entice unsuspecting employees to download innocent looking files or click on malicious links and infect computers with spyware, viruses, or ransomware.
“Phishing attacks are one of the most common and damaging ways for hackers to access your systems,” Mr. Nachbahr explains. “Your employees should be the frontline defense against attack — your ‘human firewall’. Ongoing employee training, education, and support allows them to recognize social engineering attacks and thwart costly episodes before they begin.” Preventative measures include:
- Web filters and controls that restrict access to
phishing links - Multi-factor authorizations for wire transactions
- Limits on payment amounts that a single employee
can authorize - Cloud backup for restoration following a malicious software attack
- Intrusion detection software to identify suspicious network activity
- Web filters and controls that restrict access to
- Synthetic identity fraud is another risk to dealers today. Imposters use fake information to create fictitious identities, combining stolen identity information to create new credit files. These new synthetic identities allow criminals to qualify for a loan to buy vehicles, putting dealerships at risk for losses. Background checks verifying customer identity offer the best protection.
When cyber fraud does penetrate a dealership, speed is the key to mitigating its impact — the faster an attack in progress can be detected and stopped, the less its damage. Quick detection and speedy remediation deploys an entire set of technologies, processes, and expertise — including digital forensics, threat hunting, malware reverse engineering, and technical surveillance countermeasures — that most dealers don’t have. Mr. Nachbahr explains, “Dealers need a Security Operation Center (SOC) to monitor the network 24/7/365 looking for signs of malicious behavior. Tools like advanced endpoint threat protection and security information event management (SIEM) allow security professionals to sift through and correlate data and identify suspicious patterns of behavior so they can shut down the attack early and limit damage to the dealer.
“Dealers are quickly recognizing the need for a SOC, but security professionals with the training and certification to run the centers are hard to find. Most dealers are turning to outsourcing to protect their business.”
Cyber Liability Insurance
Cyber liability insurance protects your dealership when cybercrime happens. “Many dealers don’t think cybercrime will happen to them and are not prepared when it does,” explains J. Travis Johnson, Auto Dealer Practice Leader at McGriff Insurance, a subsidiary of Truist Insurance Holdings, Inc. “Due to their systems and transaction levels, dealers are one of the many low-hanging fruits for cyber criminals. While some OEMs do require cyber liability insurance, dealers who aren’t required to purchase policies typically don’t think the premium money spent is worth it. Not realizing the overall benefit of a cyber liability policy is relatively inexpensive when compared to the damage a cyberattack can cause.”
Dealerships interested in cyber insurance policies undergo an extensive cyber risk review that rates them on existing cybersecurity vulnerabilities and defenses in place. Your level of cybersecurity preparation determines your premiums. Some of the coverages include the cost of identifying where the attack came from, making ransom payments, paying rewards for informants, repairing or replacing computer hardware, and potential court costs. If an attack happens, most insurance carriers offer a 24/7 on-call teams to advise you on next steps and help you get the problem resolved as quickly as possible so you can get up and running again.
Don’t Think You Are Flying Under the Radar
Headline-making data breaches typically occur at large, well-known companies, but that doesn’t mean your dealership can rest easy. Fraud criminals are constantly looking for the easiest marks, and sizeable transaction volumes combined with disparate systems make dealerships particularly vulnerable. Take protection measures seriously to avoid being a victim.
Can I Afford to Ignore Cybercrime?
A serious cybercrime attack can be crippling. A ransomed network, infected server, or compromised bank account can be as much of a disaster as a flood or fire. As more dealerships rely on digital customer interactions and transactions, the benefits of protecting your dealership, your data, and your finances from fraudulent activity have never been greater.
Don’t Let Cybercriminals Steal Your Business
Talk to your relationship manager or treasury consultant to discuss your business plans and your dealership’s fraud defenses, including ways to mitigate damages through McGriff Automotive insurance policies.
Keep up with the digital buying transformation. Talk to your Truist Dealer Services Officer about how Truist can help you build out your digital buying journey. Go to www.Truist.com for more details.








